遗世独立
题目

$ ./cryptooo SECCON{ } Encrypted(44): waUqjjDGnYxVyvUOLN8HquEO0J5Dqkh/zr/3KXJCEnw= what's the key?下载附件得到
由执行附件内的文件 利用信息解密
int __fastcall main(int a1, char **a2, char **a3)
{
unsigned int v4; // [rsp+2Ch] [rbp-814h]
char v5[2056]; // [rsp+30h] [rbp-810h] BYREF
unsigned __int64 v6; // [rsp+838h] [rbp-8h]
v6 = __readfsqword(0x28u);
if ( a1 <= 1 )
return 1;
memset(v5, 0, 0x800uLL);
v4 = sub_401373(a2[1], (unsigned int)strlen(a2[1]), v5, 2048LL);
return printf("Encrypted(%d): %sn", v4, v5);
}__int64 __fastcall sub_401373(__int64 a1, int a2, __int64 a3, int a4)
{
int v5; // [rsp+2Ch] [rbp-4h]
if ( a2 <= 0 )
return 0xFFFFFFFFLL;
v5 = 4 * (a2 / 3 + (a2 % 3 != 0));
if ( v5 > a4 )
return 0xFFFFFFFFLL;
sub_400FCE(a1, (unsigned int)a2, a3);
return (unsigned int)v5;
}unsigned __int64 __fastcall sub_400FCE(__int64 a1, signed int a2, __int64 a3)
{
unsigned __int64 result; // rax
unsigned __int64 v5; // [rsp+28h] [rbp-68h]
unsigned __int64 v6; // [rsp+28h] [rbp-68h]
unsigned __int64 v7; // [rsp+28h] [rbp-68h]
int v8; // [rsp+30h] [rbp-60h]
int i; // [rsp+34h] [rbp-5Ch]
int v10; // [rsp+3Ch] [rbp-54h]
int v11[18]; // [rsp+40h] [rbp-50h] BYREF
unsigned __int64 v12; // [rsp+88h] [rbp-8h]
v12 = __readfsqword(0x28u);
qmemcpy(v11, "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/", 64);
sub_400F3A(v11, 64LL, a1, a1, (unsigned int)a2);
v10 = a2 % 3;
v8 = 0;
for ( i = 0; ; ++i )
{
result = (unsigned int)v8;
if ( v8 >= a2 / 3 )
break;
v5 = *(unsigned __int8 *)(a1 + 3 * v8 + 2LL) | ((*(unsigned __int8 *)(a1 + 3 * v8 + 1LL) | ((unsigned __int64)*(unsigned __int8 *)(a1 + 3 * v8) << 8)) << 8);
*(_BYTE *)(a3 + 4 * i) = *((_BYTE *)v11 + ((v5 >> 18) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 1LL) = *((_BYTE *)v11 + ((v5 >> 12) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 2LL) = *((_BYTE *)v11 + ((v5 >> 6) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 3LL) = *((_BYTE *)v11 + (v5 & 0x3F));
++v8;
}
if ( v10 > 0 )
{
if ( v10 == 1 )
{
v6 = (unsigned __int64)*(unsigned __int8 *)(a1 + 3 * v8) << 16;
*(_BYTE *)(a3 + 4 * i) = *((_BYTE *)v11 + ((v6 >> 18) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 1LL) = *((_BYTE *)v11 + ((v6 >> 12) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 2LL) = 61;
result = a3 + 4 * i + 3LL;
*(_BYTE *)result = 61;
}
if ( v10 == 2 )
{
v7 = (*(unsigned __int8 *)(a1 + 3 * v8 + 1LL) | ((unsigned __int64)*(unsigned __int8 *)(a1 + 3 * v8) << 8)) << 8;
*(_BYTE *)(a3 + 4 * i) = *((_BYTE *)v11 + ((v7 >> 18) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 1LL) = *((_BYTE *)v11 + ((v7 >> 12) & 0x3F));
*(_BYTE *)(a3 + 4 * i + 2LL) = *((_BYTE *)v11 + ((v7 >> 6) & 0x3F));
result = a3 + 4 * i + 3LL;
*(_BYTE *)result = 61;
}
}
return result;
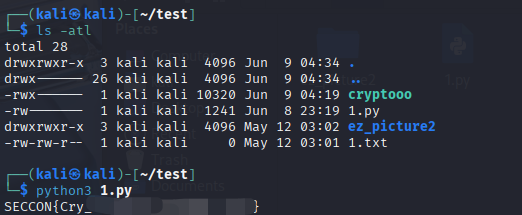
}倒入 kali 中确认已经安装 python
python3 --version
路径下需要有 python 代码文件和 cryptooo 可执行文件
更新: 2025-06-09 17:25:59
原文: https://www.yuque.com/yuhui.net/network/clgvqe5va6t6uapx


评论(0)
暂无评论